Whatever Conflicts May Come
1) A new service appears to host at client site which we had never seen before. No recorded presence about it online.
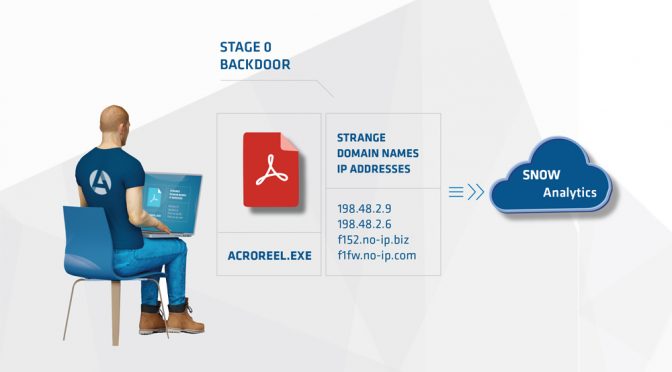
2) Our analysts fetch the file and immediately begin reverse engineering it. It’s immediately apparent this is a Stage 0 (initial malware used during an advanced attack).
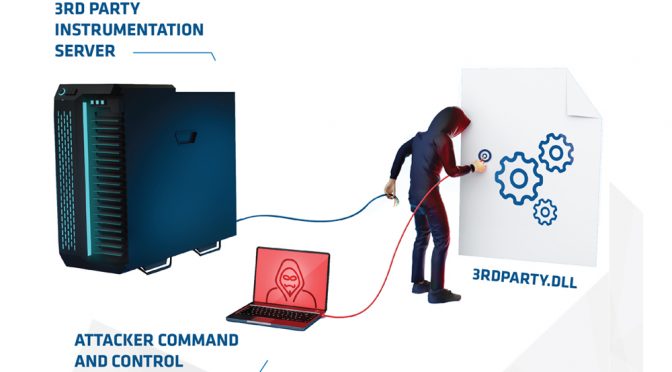
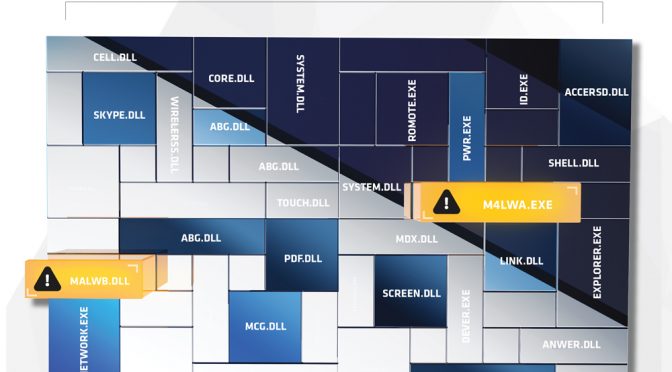
3) Through their reverse engineering, they extract several components of interest that are unique to this malware. Mutexes, file names, memory strings, types of command lines, byte patterns, domains etc.
4) The analyst immediately begins feeding those characteristics back into Arc4dia’s systems and is able to identify two other completely different pieces of malware present on other systems that have a least one characteristic in common. One is a standalone executable and the other one has no other presence than in memory injected in another process.
5) With three different versions identified, the analyst disabled them by killing the processes and relevant threads.
6) The client is contacted and given the location and nature of the compromise. A list of network characteristics is also provided so that the existing security team can attempt to correlate the malicious activity across all of their assets.
Beyond the detection of a malicious program, Arc4dia has the means to look for similar and familiar malware patterns, and stop the full attack at the root.